What is Mimikatz?
If you’re into penetration testing and windows red teaming then you might have probably heard of mimikatz, but in case you’re wondering or have heard of the tool but don’t know what it does, let’s see what is mimikatz.
Written in C-language, Mimikatz is a very powerful post-exploitation tool and as described by CrowdStrike CTO and Co-Founder, “The AK-47 of Cyber Attacks.”
Some even claim mimikatz to be a Swiss Army Knife of Windows Credentials. Benjamin Delpy, who is the developer of this tool, claims that he created this tool to play with Windows Security. He maintains his own GitHub repository where he has provided the source code for the tool and updates it on a regular basis.
What can be done using Mimikatz?
Although known widely for credential dumping, this is not the only thing that it can do.
Mimikatz is also capable of assisting in lateral movements and privilege escalations. Attacks like Pass-the-Hash, Pass-the-Ticket, Over-Pass-the-Hash, Kerberoasting etc. can also be achieved with Mimikatz.
Mimikatz Attack Capabilities
Mimikatz has numerous modules that let attackers perform a variety of tasks on the target endpoint. Some of the more important attacks facilitated by the platform are:
- Pass-the-Hash—obtains an NTLM hash used by Windows to deliver passwords. This allows attackers to reuse the password without having to crack the hash.
- Pass-the-Ticket—Mimikatz was famously used to break the Kerberos protocol. It can obtain a Kerberos “ticket” for a user account and use it to login as that user on another computer.
- Kerberos Golden Ticket—obtains the ticket for the hidden root account (KRBTGT) that encrypts all authentication tickets, granting domain admin access for any computer on the network.
- Kerberos Silver Ticket—exploits Windows functionality that grants a user a ticket to access multiple services on the network (via the Ticket Granting Server or TGS). The Kerberos protocol may not check the TGS key, allowing attackers to reuse the key and impersonate the user on the network.
- Pass the Key—obtains a unique key used by a user to authenticate to a domain controller. The attacker can reuse this key to impersonate the user.
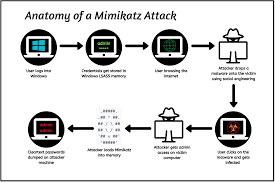
Anatomy of a Mimikatz Attack:
Mimikatz abuses and exploits the Single Sign-On functionality of Windows Authentication that allows the user to authenticate himself only once in order to use various Windows services.
After a user logs into Windows, a set of credentials is generated and stored in the Local Security Authority Subsystem Service (LSASS) in the memory. As the LSASS is loaded in memory, when invoked mimikatz loads its dynamic link library (dll) into the library from where it can extract the credential hashes and dumps them onto the attacking system, and might even give us cleartext passwords.









0 comments:
Post a Comment